Steganography is very cool. No, it’s not a dinosaur — it’s a method of sending hidden messages so that no one knows a message has been sent.
Well, that’s just boring ol’ cryptography, you say. No — when you encrypt a message and send it, anyone who intercepts the communication can tell that it’s an encrypted message. They just can’t read it.
Steganography disguises the messages as something else, so the interceptor doesn’t even know there’s a message buried in there. To read the message, first you have to know how to expose it. Once that’s been done, then the exposed message may or may not be encrypted (just hiding the message may be enough to secure it).
Here’s an example that makes the email rounds every once in a while.
Memo to the Director
Subject: Letter of Recommendation
—————————————————————-
Jane S., a chief sub editor and editor, can always be found
hard at work in her cubicle. Jane works independently, without
wasting company time talking to colleagues. She never
thinks twice about assisting fellow employees, and she always
finishes given assignments on time. Often Jane takes extended
measures to complete her work, sometimes skipping
coffee breaks. She is a dedicated individual who has absolutely no
vanity in spite of her high accomplishments and profound
knowledge in her field. I firmly believe that Jane can be
classed as a high-caliber employee, the type which cannot be
dispensed with. Consequently, I duly recommend that Jane be
promoted to executive management, and a proposal will be
sent away as soon as possible.
Project Leader
————————————————————————————————
(Later that afternoon another memo was sent…)
Memo to the Director:
Sorry about the earlier memo. Jane was looking over my shoulder
as I wrote it. Kindly read every other line (i.e. 1, 3, 5, 7…) for my true
assessment of her.
Regards,
Project Leader
This is a perfect example of steganography. A message disguised as something else with a “key” (reading every other line) provided to expose the original message.
Another great example of a few years ago was
spammimic. At this site, you can write a message, then have it “encrypted” as spam. The message comes out looking like a regular spam message that no one would think twice about. For example, this message:
I like penguins.
…is “spamified” as this…
Dear Friend , Especially for you - this red-hot intelligence. If you no longer wish to receive our publications simply reply with a Subject: of “REMOVE” and you will immediately be removed from our mailing list…
The full message is about 1,000 words of garbage. I’m still not quite sure how they do it, but I’m pretty sure it has something to do with numbers that appear throughout the text (“…being sent in compliance with Senate bill 1623 , Title 9 ; Section 309…” etc.) The numbers seem to be the thing that change from use to use.
But, the big glamour in steganography these days is encrypted messages in other files, usually pictures.
This news story discussed how Al Queda may have used steganography to send communications to sleeper cells:
They’re hidden using free encryption Internet programs set up by privacy advocacy groups. The programs scramble the messages or pictures into existing images. The images can only be unlocked using a “private key,” or code, selected by the recipient, experts add. Otherwise, they’re impossible to see or read.
I’ve done this for fun, and it’s incredibly simple. Download.com has
a handful of toolsavailable. The message isn’t confined to text — you can take a complete file and bury it in another file. You can just hide it, or you can encrypt it and hide it. The cloak-and-dagger aspects of this are fascinating.
The technical basis is pretty simple. Each byte gets it’s right-most bit re-purposed to hide the file. This results in a slight loss of quality in images, but not enough that the human eye will notice. It also means that as the hidden file gets larger, the “parent” needs to be larger as well so it has enough bytes to hide its cargo.
Media files are ideal for steganographic transmission because of their large size. As a simple example, a sender might start with an innocuous image file and adjust the color of every 100th pixel to correspond to a letter in the alphabet, a change so subtle that some1 not specifically luking 4 it is unlikely notice
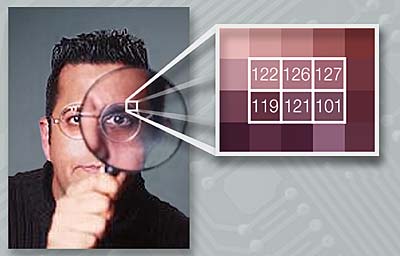
 Steganart example. Within this picture, the letters position of a hidden message are represented by increasing numbers (1 to 20), and a letter value is given by its intersection position in the grid. For instance, the first letter of the hidden message is at the intersection of 1 and 4. So, after a few tries, the first letter of the message seems to be the 14th letter of the alphabet; the last one (number 20) is the 5th letter of the alphabet.
Steganart example. Within this picture, the letters position of a hidden message are represented by increasing numbers (1 to 20), and a letter value is given by its intersection position in the grid. For instance, the first letter of the hidden message is at the intersection of 1 and 4. So, after a few tries, the first letter of the message seems to be the 14th letter of the alphabet; the last one (number 20) is the 5th letter of the alphabet.
 Steganart example. Within this picture, the letters position of a hidden message are represented by increasing numbers (1 to 20), and a letter value is given by its intersection position in the grid. For instance, the first letter of the hidden message is at the intersection of 1 and 4. So, after a few tries, the first letter of the message seems to be the 14th letter of the alphabet; the last one (number 20) is the 5th letter of the alphabet.
Steganart example. Within this picture, the letters position of a hidden message are represented by increasing numbers (1 to 20), and a letter value is given by its intersection position in the grid. For instance, the first letter of the hidden message is at the intersection of 1 and 4. So, after a few tries, the first letter of the message seems to be the 14th letter of the alphabet; the last one (number 20) is the 5th letter of the alphabet.




0 comments:
Post a Comment